Row-hammer security vulnerability is a fault in DRAM modules in computers
Random access memory (RAM) is a key component that impacts computers’ performance. RAM provides applications with a place to store and access data on a real-time basis. Dynamic RAM (DRAM) is a common type of RAM currently used in desktops and laptops. Despite years of research, DRAM systems are increasingly plagued by Row-Hammer (RH) security vulnerability. Current RH solutions that rely on static RAM (SRAM) incur impractical storage overheads that are not appealing for commercial adoption. Other solutions that store per-row metadata in the RAM space cause significant slowdown in performance. As such, there is a need for a viable solution to mitigate RH, as DRAM is a commodity part widely used in all computer systems.
A hybrid tracker provides low-cost RH mitigation at low thresholds
Hydra, a hybrid tracker for RH mitigation, combines the best of both SRAM and DRAM to enable low-cost RH mitigation at ultra-low thresholds. Hydra is composed of two structures: (1) an SRAM-based structure that tracks aggregated counts of a group of rows and (2) a per-row tracker stored in the DRAM array that is only used for the small number of rows that exceed the tracking capability of the SRAM-based structure. Using the per-row tracker in this way limits performance overheads. Hydra enables robust RH mitigation while incurring an SRAM overhead of only 28 KB per-rank and an average slowdown of only 0.7%.
- Complete solution: Hydra combines the best of SRAM-tracking (low performance overhead) and DRAM-tracking (low SRAM overhead and flexibility of tracking all rows) to produce the only RH mitigation that is effective at ultra-low thresholds.
- Proven robust security results: By looking at the aggregate count and specific rows of data, Hydra provides system analysis that successfully mitigates RH security vulnerability.
- Cost-effective: Compared to existing technologies, Hydra is low cost in terms of both storage and performance.
- Maintains system functionality: Hydra is effective and does not compromise the functionality of the system because the slowdown is so low.
DRAM is a commodity part that is commonly found in computer systems. As such, Hydra is widely applicable to mitigating RH security vulnerability across computer systems and consumer electronic devices, such as smart phones, digital TVs, set-top and gaming boxes, digital still and video cameras, hard disk drives, printers, storage and networking equipment, automotive, appliances, and many others.
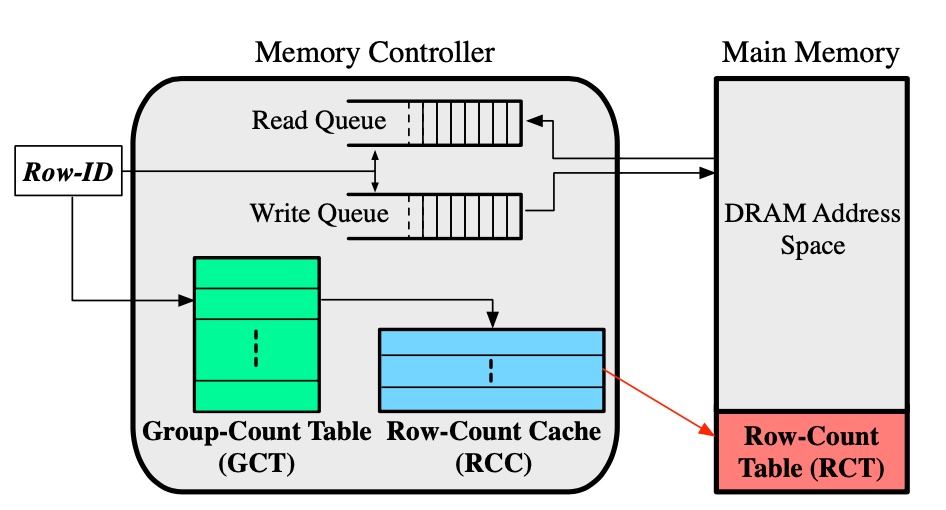
Overview of Hydra. Hydra splits tracking into two parts: (a) Aggregated tracking using GCT (b) Per-row tracking using RCT (cached in RCC).
