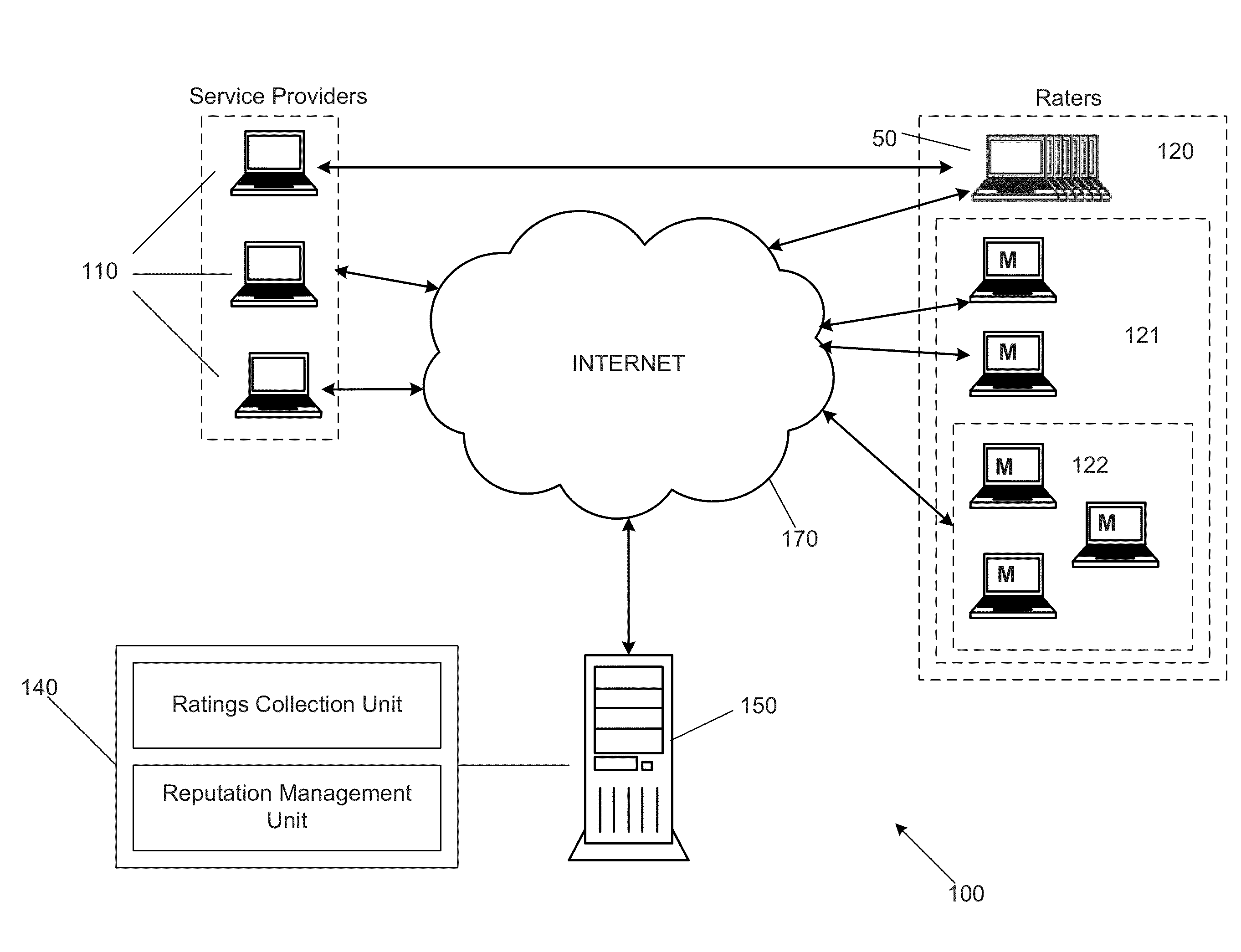
Georgia Tech inventors have developed the Belief Propagation based Iterative Trust and Reputation Management Scheme (BP-ITRM) — an algorithm that analyzes buyer-seller interactions as well as consumer ratings and accurately computes the associated reputation values. The BP-ITRM includes receiving a large number of ratings. Each rating is associated with a service provider and a rater. The method also includes modeling the service providers, the raters, and the ratings as a factor graph representing the factorization of a joint probability distribution function of variables, calculating the marginal distributions using a belief propagation algorithm applied to the factor graph, and determining reputation values associated with the service providers and trustworthiness values associated with the raters based on the calculating.Lastly it also accurately, robustly, and efficiently detects and filters out malicious raters whose trustworthiness is then updated accordingly.
- Robust to attacks
- Computational efficiency
- Detects malicious ratings
- Automatic web services selection
- Human networks (collaborative information exchange sites such as Expert Systems, Community Question Answering, etc.)
- E-commerce and online services and transactions
- Any type of co-operative networks (e.g. peer-to-peer, wireless end-to-end, ad-hoc networks, delay tolerant mobile networks, intermittently connection networks) that are prone to attacks or selfish behavior of nodes
The growth of the internet and social media, along with the rapid development of software, have made trust and reputation management a core tool in managing an individual's or group's reputation.Trust management systems are used to assist entities that have to interact with others in a system, especially in the decision making process. These reputations are often built by prior consumer’s reports of a service or product, which can often be unreliable or intentionally malicious. Most well-known commercial websites use reputation mechanisms, but there is a need for more reliable schemes in the face of system attacks.